linkedin-skill-assessments-quizzes
IT Operations
Q1. You are configuring a Wi-Fi base station using DHCP. Which items should you set or change?
-
A
- Reset administrator password.
- Set network name.
- Set network security.
-
Set network password.
-
B
- Reset administrator password.
- Set network name.
-
Set network password.
-
C
- Set network name.
- Set network password.
-
Assign DNS servers.
-
D
- Change administrator account name.
- Set network password.
- Set network name.
- Assign DNS servers.
Q2. Can you connect a DisplayPort monitor to a USB-C port on your computer?
- Yes. The DisplayPort cable plugs directly into the USB connector.
- Yes. An adapter or dongle may be required.
- No. While you can rig a connection, video quality will be poor.
- No. The two standards are incompatible.
Q3. What is the I/O panel?
- the location where expansion cards can connect to peripherals
- a cluster of ports and connectors found on the back of the computer case
- the switches that turn on, sleep, and turn off the computer
- the portion of the motherboard where non-power cables connect
Q4. The computer consistently boots into Safe Mode. How would you address this issue?
- Edit the Registry key that controls the boot sequence.
- Hold the Shift key as Windows boots.
- Check the MSCONFIG utility to ensure that Normal boot is selected.
- Fix the issue in Safe Mode that is causing the system to restart in this mode.
Q5. Which choice is not a typical adjustment found on a monitor?
- resolution
- color temperature
- contrast
- brightness
Q6. Assuming that the gateway, modem, and switch are separate units, in what order should a small office or home office LAN be restarted?
- A
- Modem
- Gateway
- Switch
- B
- Modem
- Switch
- Gateway
- C
- Gateway
- Switch
- The order is not important.
Q7. A client needs to secure their cafe’s wireless network, which is used only by employees. What is the best approach for a finite list of devices?
- Limit access to specific MAC addresses.
- Do not broadcast the SSID.
- Apply a metered connection.
- Apply a password.
Q8. Which hardware port would not be found on a typical gateway?
- WAN
- USB
- LAN
- uplink
Q9. The recent Windows update introduced some quirks in the system. How can you enter the Windows Recovery Environment to recover from the update?
- Hold the Shift key when selecting the Restart command.
- Restart in Safe Mode where the Recovery item is located on the Start menu.
- Press the any key at the boot screen.
- Go to the Task Manager Startup tab.
Q10. Which components are typically found on the motherboard?
-
basic I/O graphics NIC battery expansion slots
-
basic I/O cooling NIC graphics expansion slots
-
basic I/O graphics NIC mass storage expansion slots
-
basic I/O graphics NIC power supply expansion slots
Q11. What does the acronym RAID refer to?
- Repeating Architecture for Internal Drives
- Recoverable Advanced Integration and Duplication
- Redundant Array of Independent Disks
- Replicated Array of Internal Devices
Q12. To which internal component does the illustrated (P1) connector attach?
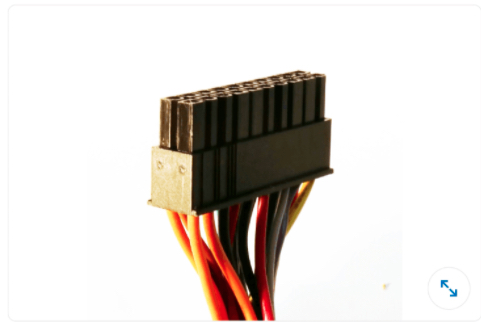
- motherboard
- I/O panel
- power supply
- primary mass storage
Q13. Your computer boots at very low resolution that cannot be increased through display settings. What is the most likely solution?
- The connection between the display and the computer is loose.
- You need to reinstall the display drivers.
- You need to replace your monitor.
- Some of your RAM is failing.
Q14. To which choice can the wget program be considered similar?
- tracert
- netstat
- ping
- cURL
Q15. Does an incognito window prevent websites from tracking your activity on the web?
- No. Incognito mode only prevents the site from appearing in your browser history.
- Yes. Incognito mode encrypts data packets, making it difficult for websites to track your activity.
- No. Some websites track by ID, and if you sign into a site even in incognito, your activity is known.
- Yes. Incognito mode blocks all cookies and tracking IDs and suppresses browser history.
Q16. What must you confirm before performing a processor upgrade?
- The new processor is compatible with the current motherboard.
- The new processor is the same type as the old.
- The new processor is compatible with the operating system.
- The new processor fits into the old processor’s slot.
Q17. Which type of storage has the fastest data access speeds?
- Secure Sockets Layer drive
- solid-state drive
- serial attached storage device
- SCSI drive
Q18. Which peripheral is most likely to require entering a Bluetooth pairing passcode?
- A. Keyboard
- B. Mouse
- C. Headset
- D. Printer
Explanation: Many Bluetooth keyboards (especially older or “legacy” models) require entering a pairing/passcode during initial pairing. Mice and headsets can require pairing too, but keyboards historically + most commonly use a numeric pairing code. This question is somewhat hardware-dependent — see PR discussion for edge-cases and references.
Q19. Walt’s computer is several years old and he wants to ensure that the system works until he gets a replacement. What should he do first?
- Run a file check daily.
- Obtain an extended warranty.
- Back up his data.
- Ensure that the system is protected against malware.
Q20. Which statement best describes a drive?
- A. A drive is hardware that reads/writes data and often accepts removable media (e.g., disk, CD).
- B. A drive is a software component that manages files.
- C. A drive is a network service for file transfer.
- D. A drive is an encryption method.
Explanation: A drive is a physical device that performs read/write operations; removable-media drives (CD/DVD, removable disk) accept media, while non-removable drives (SSD/HDD) provide storage without separate media.
Q21. Mass storage inside a desktop computer case is usually found where?
- in an expansion slot
- attached to the front of the case
- in a drive cage
- on the motherboard
Q31. Which device is used to connect computers on a local network (LAN) at Layer 2?
- A. Switch (Layer 2)
- B. Server
- C. Router
- D. Gateway
Explanation: A network switch operates at Layer 2 and forwards frames between devices on the same LAN. Servers provide services but do not serve the traffic-forwarding role of a switch.
Q43. If you move a user’s data and installed programs from one system to another, this process is called:
- A. Migration
- B. Profile transfer
- C. Backup
- D. Restore
Explanation: A migration moves data and installed applications/settings from one environment to another; a “profile transfer” generally refers only to user profile data.
Q51. To access extra keys or alternate key functions on some laptop keyboards (compact layouts), which key is typically used?
- A. Alt/Option
- B. Ctrl
- C. Fn
- D. Shift
Explanation: The Fn (Function) key is commonly used to access alternate functions on laptop/compact keyboards (media keys, secondary key legends). Alt/Option performs different roles and is not the usual way to access alternate hardware keysets.
Q52. If a PC repeatedly boots into Safe Mode, what is the most appropriate next step?
- A. Reboot immediately and hope it resolves.
- B. Investigate the cause (Safe Mode indicates the system detected a problem).
- C. Reinstall the OS right away.
- D. Ignore and continue using.
Explanation: Persistent boots into Safe Mode indicate underlying problems (driver, hardware, or config). Investigate logs, recent changes and safe-mode diagnostics before opting to reinstall or only restart. (A quick restart can be used as a test, but repeated Safe Mode boots should be diagnosed.)
Q53. Which security tool can be doubled up to offer additional protection without being redundant?
- account protection
- firewall
- antivirus
- backup
Q54. The mouse pointer is behaving erratically. What should you do first?
- Use the keyboard instead
- Restart the computer
- Clean the mouse, specifically its optical sensor, and ensure that you are using it on the proper surface
- Disassemble the mouse to look for loose parts or corrosion
Q55. How many wire pairs are in a CAT-5 cable?
- 8
- 4
- 5
- 16
Q56. What is the difference between a USB hub and a powered USB hub?
- The powered hub has a power supply and is suitable for running powered peripherals.
- A powered USB hub is found on the computer case; all other hubs are non-powered.
- The powered hub supplies 12V of power, whereas the standard hub only 5V.
- Powered hubs are external to the computer case.
Q57. Which of the following users has the smartest approach to online security?
- Jarred uses a unique password for each site.
- Jen uses the same password on each site, but with two-factor authentication.
- Jason uses a unique password for each site along with two-factor authentication.
- Jackie uses the same password on each site, but with a different user name.
Q58. Which is an example of a phishing attack?
- Yousef sees an onscreen notification indicating that an operating system is pending and instructing him to click a link to continue.
- After visiting a website, Carla notices that her computer is running slowly.
- Bob receives an email from his bank, asking him to click a link to verify his account.
- Ellen’s email inbox is flooded with unwanted advertising.
Q59. You receive a malware warning regarding a specific file. Which approach should you take to ensure that you do not have false positive?
- Restart in Safe Mode to remove the file.
- Remove the file.
- Run a thorough scan to validate the results.
- Quarantine the file.
Q60. What are the best tools to use for cleaning a computer?
- Handheld vacuum cleaner, air can, soft flashlight.
- air can, microfiber cloth, alcohol wipes, flashlight.
- handheld vacuum cleaner, ammonia, alcohol, microfiber cloth.
- air can, screwdriver, soft cloth, household cleaner.
Q61. A computer power supply is measured in _.
- watts
- hertz
- amperes
- volts
Q62. If you had a 255.255.255.0 subnet mask, how many usable IP addresses would you have for hosts?
- 24
- 255
- 254
- 256
Q63. Tania was told to change a setting in the UEFI. How is it accessed?
- by using the System Configuration Utility (MSCONFIG)
- from the BIOS
- from the computer’s startup menu
- on the network
Q64. What is the technical reason why you must properly eject media?
- File I/O is buffered. If you remove the media before the buffer is cleared, files remain open and potentially corrupt.
- The Storage Inventory Manager (SIM) can lose its drive references, which may corrupt other storage in the system.
- The drive must receive the eject signal and turn itself off, dropping the DTR signal and indicating the media is safe to remove.
- The computer must stop the 5-volt signal to media, otherwise the drive may short.
Q65. Which part of the network assigns an IP address?
- the modem using TCP/IP protocol
- the gateway/router using DHCP
- the device’s NIC based on the MAC address
- IP addresses are always assigned manually
Q66. Expansion cards follow which current interface standard?
- MCA
- PCMCIA
- ISA
- PCIe
Q67. Which action triggers a UAC warning?
- all settings changes in Windows
- any unauthorized access to the computer system
- an attempt to change a setting with consequences that affect the entire system
- any action involving the user account, such as a password reset
Q68. Which choice is not a current mass storage type?
- SSD
- MO
- HDD
- NVMe
Q69. Which statement most accurately describes the north-bridge or host-bridge?
- It is a high priority connection to the processor, also called the Memory Controller Hub.
- It has been integrated into the southbridge to provide support for the CPU.
- It is the peripheral and I/O controller, connected to the processor via the southbridge.
- It provides mathematical and 3D physics support for the CPU in the absence of a GPU.
Q70. Which characters are not allowed in a filename?
- anything other than a letter, number, or space
- spaces, periods, and commas
\, /, :, ?, and *!, ^, &, (,), and "
Q71. What is the most direct way to change the desktop background in Windows OS?
- Alter your user account settings or preferences.
- Right-click a blank part of the desktop.
- Run programs full-screen.
- Use Settings (Windows) or Preferences (Mac).
Q72. Which I/O components are typically found in a chipset on the motherboard?
- USB, SATA and internal communications
- display adapter, networking, audio, and basic I/O
- the processor, RAM, and expansion cards
- I/O components are not on the motherboard. They are located on the rear of the case
Q73. What does the acronym RAID refer to?
- Redudant Array of Independent Disk
- Repeating Architecture for Internal Drives
- Recoverable Advanced Integration and Duplication
- Replicated Array of Internal Devices
Q74. What is an example of a top-level domain (TLD)?
- NET
- HTTP
- //
- DNS
Q75. Jan is setting up a coffee shop’s wireless network. Given the number of Wi-Fi networks within range, which are the best choices for a 2.4GHz Wi-Fi channel?
- 3, 6, 9
- 3, 10, 12
- 1, 6, 11
- 1, 2, 8
Q76. When elevated access is required, what steps must a user take?
- Type the administrator account password.
- Hold the Shift key and try again.
- Sign out and sign in again with an administrator account.
- User account permissions are elevated in Settings or Preferences.
Q77. What is a duplex printer?
- a printer that also acts as a scanner, copier. and fax machine
- a printer with automatic and manual feeding mechanism
- a printer than can print on both sides of a sheet of paper
- a printer has two paper trays
Q78. Which choice is not an internal computer upgrade?
- primary storage
- I/O devices
- memory
- expansion card
Q79. In a hybrid cloud architecture, what is the main challenge of maintaining consistent configuration states across on-premises and cloud environments?
- Limited network throughput between environments
- Configuration drift due to asynchronous state management and differing IaC tool versions
- Incompatible authentication mechanisms between providers
- Lack of hardware abstraction at the virtualization layer
Q80. In enterprise IT monitoring, what problem does “cardinality explosion” refer to?
- The exponential growth in metric series when combining multiple label dimensions (e.g., host, service, region)
- The overuse of alerting thresholds across distributed systems
- The inability to track metrics due to missing time-series indexes
- The merging of multiple metric stores into a single pipeline
Q81. In a CI/CD pipeline, why is using immutable infrastructure considered best practice?
- It allows manual patching of existing servers to maintain consistency
- It ensures that each deployment creates a new environment instance, preventing configuration drift
- It eliminates the need for orchestration or automation tools
- It enables incremental updates instead of full rebuilds
Q82. What issue arises when using synchronous microservice calls in a globally distributed production system?
- Increased CPU utilization in backend servers
- Reduced need for caching layers
- Simplified tracing and logging mechanisms
- High inter-service latency and cascading failures under network partitions
Q83. In container orchestration systems like Kubernetes, what does the control plane primarily manage?
- The desired state of the cluster, ensuring workloads match declared configurations via reconciliation loops
- The real-time network routing between pods
- The physical resource allocation at the hardware level
- The filesystem synchronization across distributed nodes
Q84. In distributed systems observability, what is the primary purpose of implementing distributed tracing with context propagation?
- To record only local system metrics
- To replicate log data across all services
- To track a single request across multiple services by passing unique identifiers through each span
- To store trace data directly within the message queue
Q85. Why might an SRE team prefer a Service Level Objective (SLO) expressed as an error budget over a 100% uptime target?
- Because it balances reliability with development velocity and provides a measurable tolerance for controlled risk
- Because it enforces stricter deployment rules in CI/CD pipelines
- Because it automatically configures monitoring alerts based on uptime
- Because it eliminates the need for any downtime management
Q86. What operational issue is most likely if a message broker in an event-driven system begins showing a consistent lag in queue depth?
- Excessive horizontal scaling of producers
- Consumers are processing messages slower than the production rate, causing backpressure
- Queue visibility timeout misconfiguration
- Duplicate message publishing from producers
Q87. In large-scale infrastructure management, what’s a key operational advantage of GitOps over traditional configuration management approaches?
- It replaces container orchestration with simple shell automation
- It provides a declarative, version-controlled, and auditable single source of truth for infrastructure state
- It allows runtime state changes without version tracking
- It relies solely on imperative deployment scripts
Q88. When autoscaling a stateful application, why can horizontal scaling lead to inconsistency issues?
- Because new replicas may lack synchronized persistent state or shared volume access, leading to data divergence
- Because CPU requests cannot be adjusted dynamically
- Because vertical scaling is disabled by default
- Because service discovery protocols fail to register new instances